
In response to the great interest in OTP, we have added integration with another vendor of VPN solutions.
Sophos is another platform after Palo Alto, Pulse Secure, FortiGate and Cisco ASA for which we enable integration with NACVIEW. A new feature is a support for the Google Authenticator application to use the codes it generates. This is the second option next to one-time SMS passwords that we can use to authorize users' access to the VPN.
How does it work?
Two conditions must be met for the OTP service to work. First, Sophos must be configured in NACVIEW as a network device. The second condition is that the user has the Sophos VPN Client.
The first stage of verifying the user's identity is checking his credentials in the local NACIEW database or in an external, e.g. Active Directory. If the login and password are correct, and the account is active and the resource is properly configured, the second stage of validation takes place. NACVIEW sends the user an SMS with a verification code, or the code from the Google Authenticator app is used which must be entered into the Sophos VPN Client. After correct verification of the code and its validity, access to specific network resources is granted.
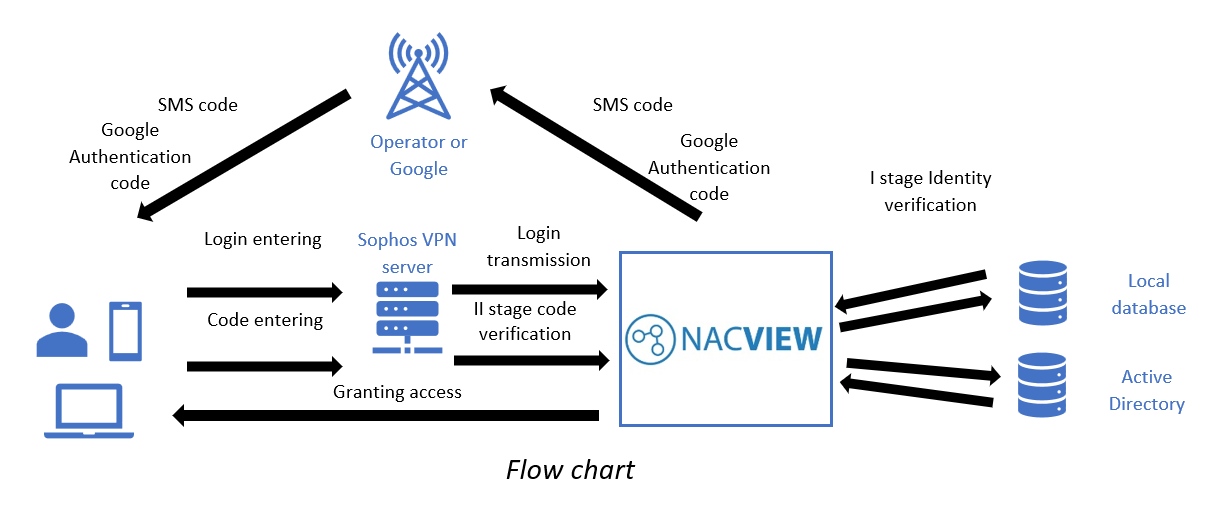
The administrator can choose additional parameters while he configuring OTP in NACVIEW, for example, code lifetime or message content. The OTP module is equipped with the ability to create object groups and display logs from authorization events.
If your company uses a different VPN solution, write to us at office@nacview.com and ask for integration.
