NAC - 100% control
The NAC (Network Access Control) system allows to manage the access of users and their devices to the corporate network. Precisely, it is the possibility of detailed control over:
- WHO? Who can access the network?
- WHAT? What device can connect to the network?
- HOW? On which network devices?
- WHEN AND WHERE? Under which conditions?
VIEW - 100% visibility
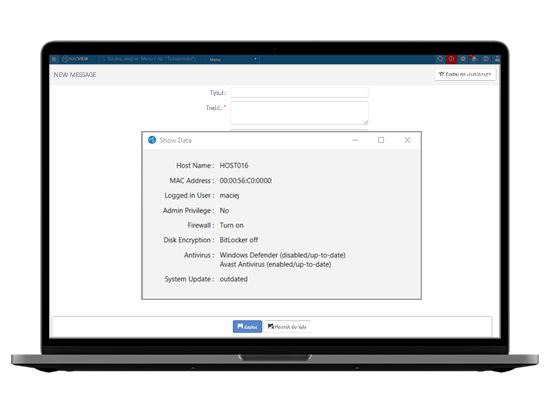
NACVIEW detects connected to the network devices in real time: both end devices and network devices with which they connect. The system has the ability to download data on end devices from external databases such as Active Directory, SQL databases, LDAP or Radius servers. Using SNMP protocols, it is possible to turn on monitoring, which allows to view the operation of devices and their load.
802.1X
A standard that provides recommendations for authenticating devices on a network. Currently, it is recognized by specialists as the most effective method of preventing unauthorized access, which significantly increases the security of the entire network.
VLAN
A technology that allows you to create multiple virtual networks on one physical network. It is a logical grouping of devices and users, e.g. based on department or job title. These groups can be created regardless of where the users are physically located.
Captive Portal
Website for the authorization of users who try to access the network. Through Captive Portal users will get to the Internet, but they will be able to use only resources specified by the administrator. There are two options in NACVIEW: configure an external Captive Portal (on network devices) or use the internal Captive Portal of the NACVIEW system.
Connection map
Automated and transparent visualization of device connections in the network. It provides a graphical representation of the network that allows to monitor which devices are connected and which are not. This allows to quickly detect network anomalies and react to them accordingly.
IPAM
IP address management, which will allow you to check the use of IP addresses, and to verify who or what device connects to a given address. This will also allow, among other things, to detect and prevent network collisions.
Threat detection
A feature that can detect incompatible, unknown or misconfigured devices. It will allow you to you to quickly find invalid network traffic (e.g. MAC / IP address cloning, port scanning, invalid gateway) and quarantine the infected device.
Solution integration
A feature that enables two-way information exchange between NACVIEW and other cybersecurity solutions. It increases the level of security by automatically responding to threats, e.g. disconnecting the device when malware is detected on it. Most often, integration concerns systems such as Firewall, UTM, MDM, SIEM, etc.
Profiling
Identification of devices connected to the network and their classification by device type (e.g. computer, telephone, printer, camera, etc.), type of operating system and manufacturer. Profiling uses many available methods, including: DHCP Fingerprinting, HTTP / S, NMAP, DNS, RADIUS.
BYOD and guest access
A solution that allows us to securely grant external users (guests) access to the network and register private devices of employees in the corporate network. Guest access can be allocated through fixed-term accounts or a dedicated portal.