Manufacturing

Manufacturing industry challenges
- Connecting all production devices to the network
- Quick response time to potential threats
- Providing technicians / service technicians with immediate access to production systems
- Separation of the office network from the production network and granting access to them according to specific rules
- Maintaining the trust of customers and contractors
Face your challenges with NACVIEW
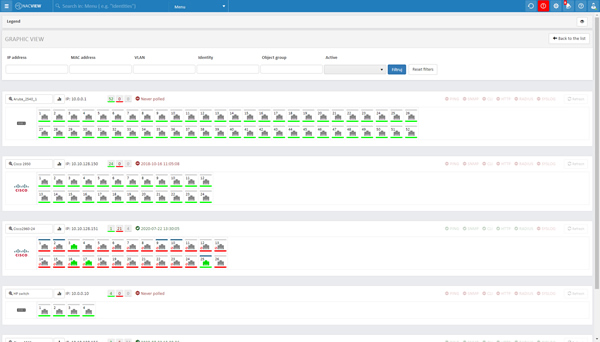
Network devices monitoring
Ensure proper operation of network devices and prevent their failure. With NACVIEW you can view detailed information about the device's health, including CPU usage, memory usage and network port load.

Alerts and automation
Receive real-time alerts about threats. NACVIEW effectively cuts off potentially dangerous devices from the network and notifies administrators about it at the same time. Such action is taken automatically on the basis of log analysis sent to the system from other security systems such as Firewall, SIEM, UTM, etc.

Double authorization validation by MAC address
Secure your ports and protect your network from any unwanted device or user. Industrial network devices usually do not have an 802.1X supplicant. Therefore, to prevent an unauthorized person from entering the production network, use the validation built into the NACVIEW system, which, thanks to appropriate protocols, verifies each device before granting access to the network.
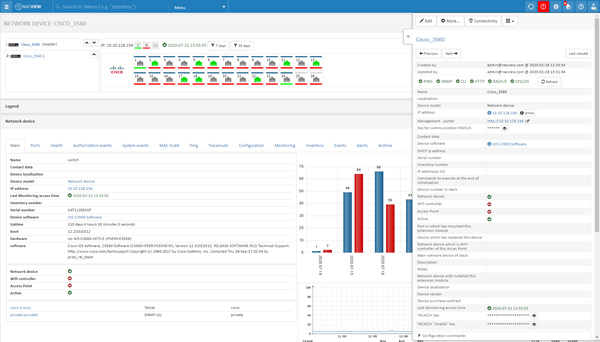
Switch configurations
Avoid network device configuration errors. NACVIEW allows you to compare the current switch configuration with the historical ones, thanks to which you will avoid configuration errors or quickly remove incorrectly introduced changes.
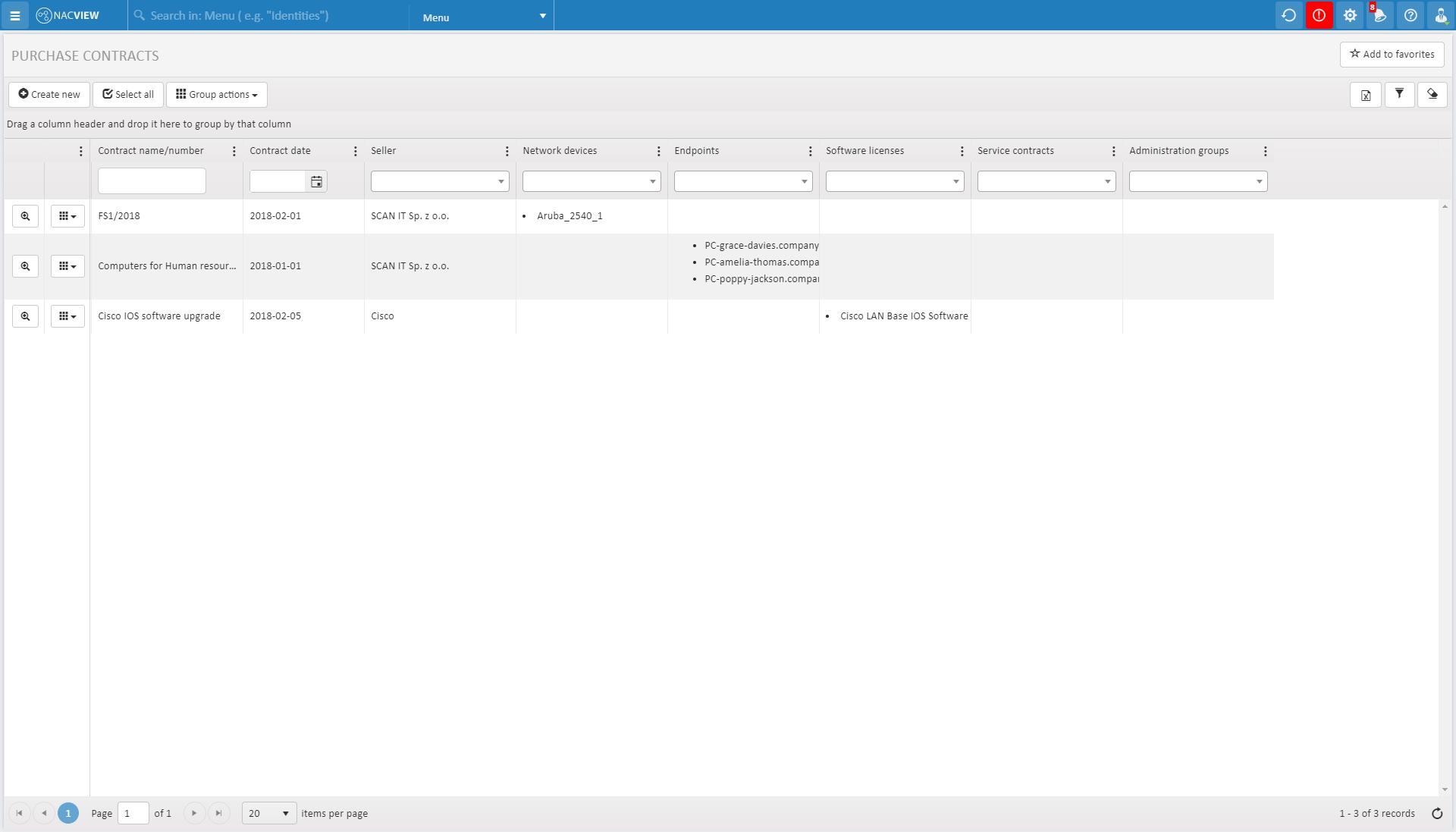
Inventory module
Remember about formalities. Thanks to a detailed inventory of all devices, an event log and tasks list, you can view the complete history of the device and never forget about end of support or a service contract.
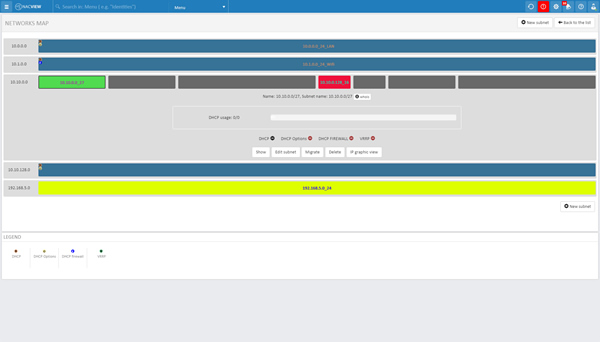
Better network segmentation
Divide the network into segments to determine the rules for accessing them. In the case of production companies, where many elements affect the proper functioning of the enterprise, network segmentation is an absolute necessity. Thanks to detailed access policies, you can assign specific devices to appropriate network areas.





