Government

Government challenges
- Protection of IT systems against attacks on confidential data
- Improve security without obstructing government services or the free flow of information
- Dedicated guest network access and BYOD policy
- Efficient and secure network access and information exchange for trusted contractors, research and public organizations
- Responsibility resulting from legal regulations and social trust
Face your challenges with NACVIEW
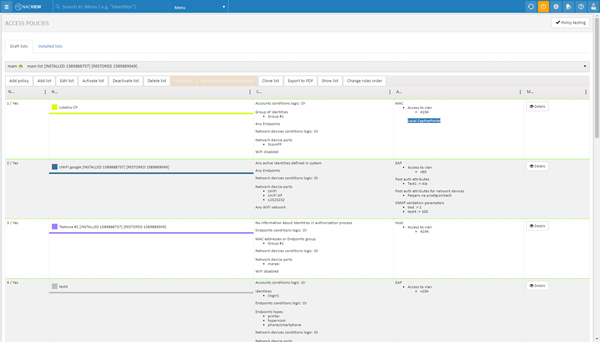
Policy enforcement based on user roles
Manage network access permissions and security compliance policies without obstructing access for employees, contractors and guests. By working with user groups and using detailed access policies, you can easily grant permissions to specific network resources.

Automatic isolation of dangerous devices
Detect potentially compromised devices and block them automatically. Administrators with multiple responsibilities have a limited response time to detected threats and it takes enough time for malware to infect the entire network before they can neutralize them. Therefore, the exchange of information between different systems is crucial, allowing for automatic isolation of dangerous devices.
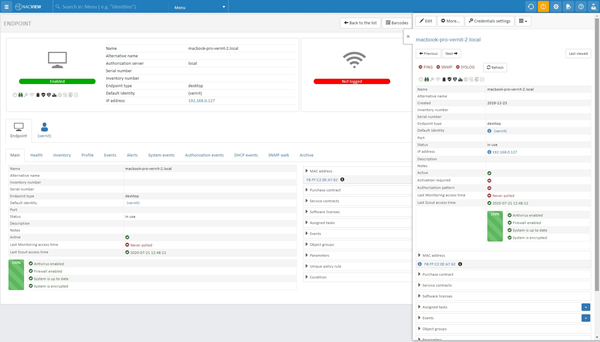
End device monitoring
Control the status of end devices in the network. Devices operating in network segments with access to critical information should be closely monitored. Thanks to the use of the NACVIEW system, you can constantly monitor the status of end devices in the network, e.g. checking the validity of anti-virus programs or verifying users logging in to a given device.
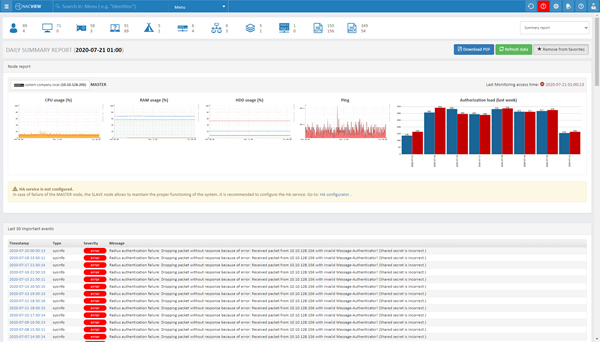
Centralized interface and detailed reports
Manage all end devices and monitor the parameters of network devices, even in distributed infrastructures. It makes work easier and faster detection of anomalies in the network. Detailed reports on system events, authorization, DHCP, TACACS, SNMP or VPN are available, allowing you to trace each event that has taken place in the network.

Reasonable BYOD
Provide network access for employees' private devices in accordance with established regulations in a controlled and safe way. Increase the productivity and satisfaction of your employees while reducing the total cost of ownership of your work mobile devices.

IoT devices security
Verify each device intended to access the network. Freestanding printers, information screens and various sensors are common targets of hackers, which, if successfully carried out, usually result in a network scan. The NACVIEW system is perfect for securing this type of device, verifying the device each time before granting it access to the network.
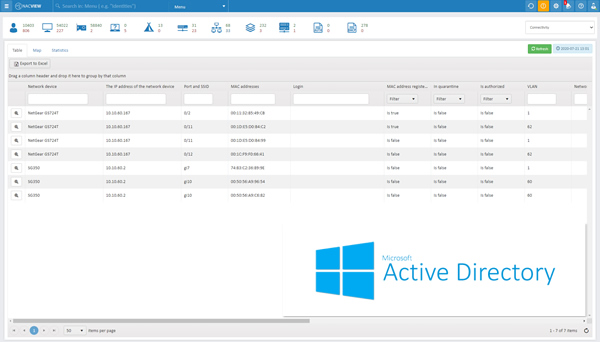
Permissions automatically granted
Automatically grant new and revoke departing employees access to the network. With NACVIEW you can manage access automatically on the basis of information transferred from AD, relational databases or other systems that store information about employees.
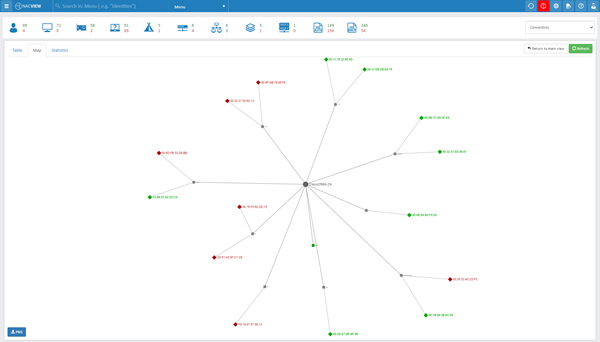
Entire network visibility
See exactly what devices connect to the government network. NACVIEW offers the unique ability to view devices instantly connecting to government networks without the need for agent software or prior device knowledge.





